
REQUEST A DEMO
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
THREATNOTE
Threatnote is an all-in-one platform that unifies intelligence, streamlines workflows, and enables your team to take action across the full threat intelligence lifecycle.
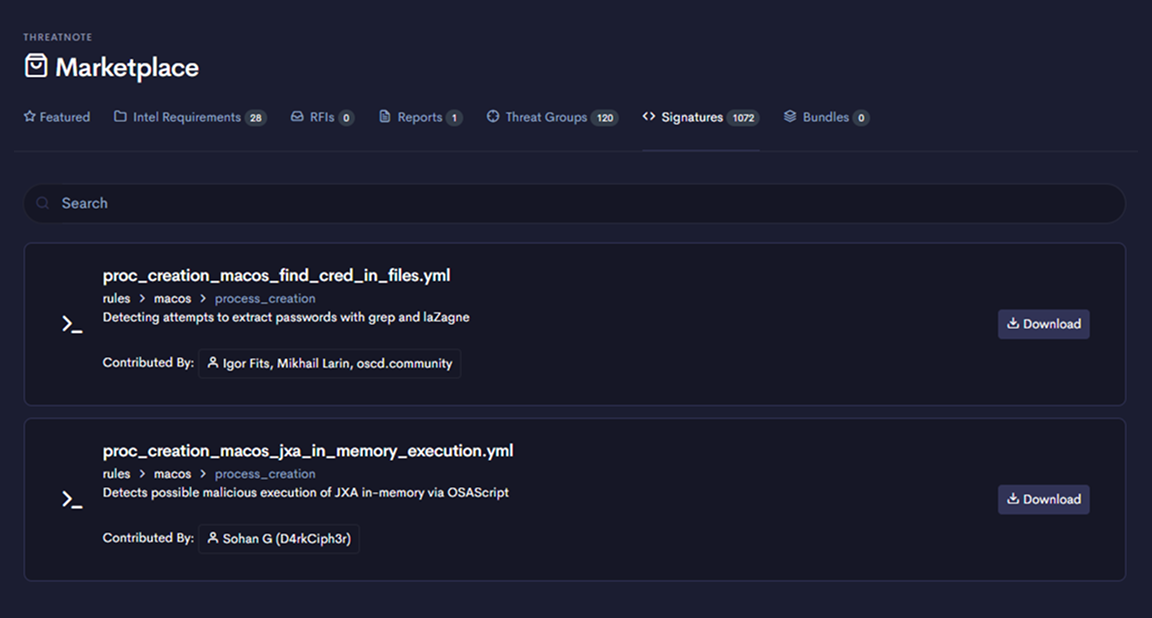



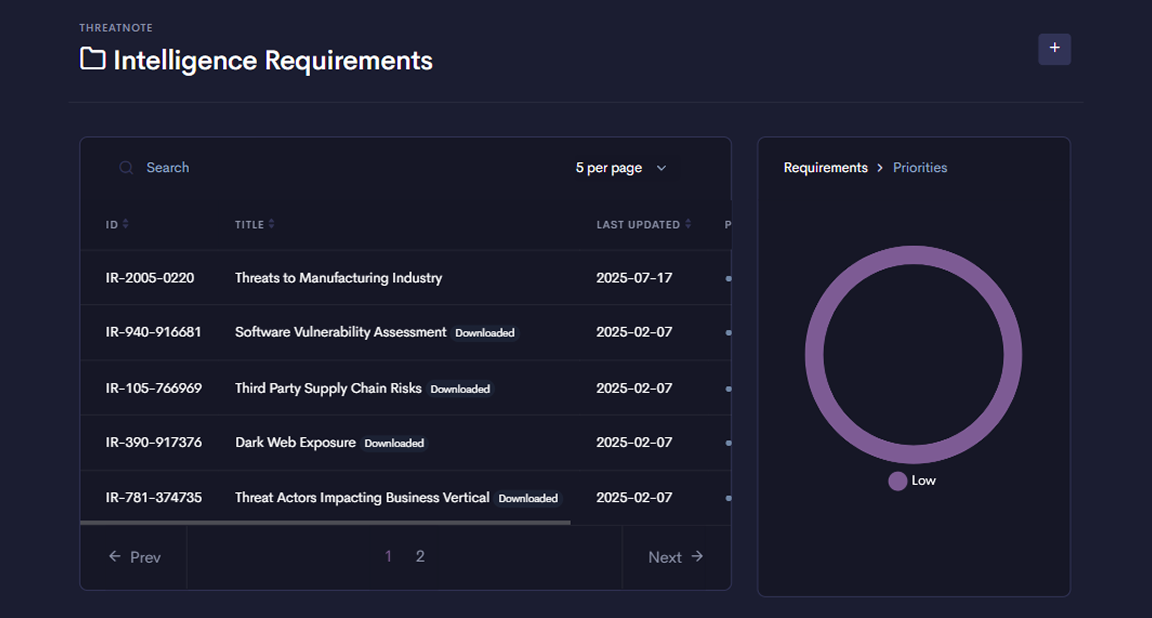



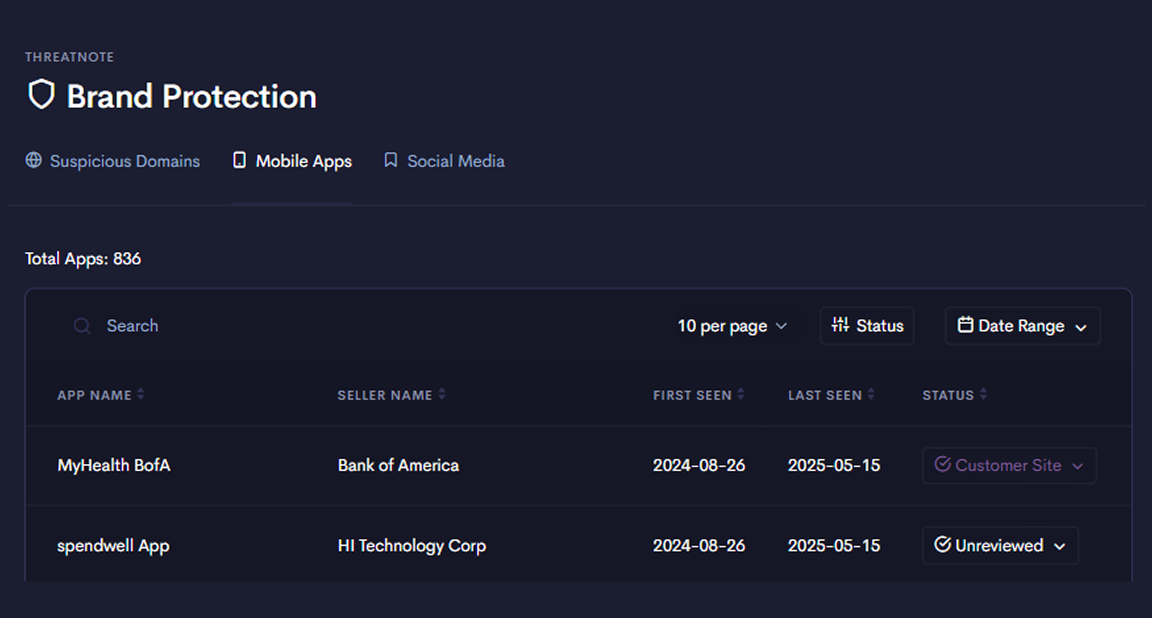



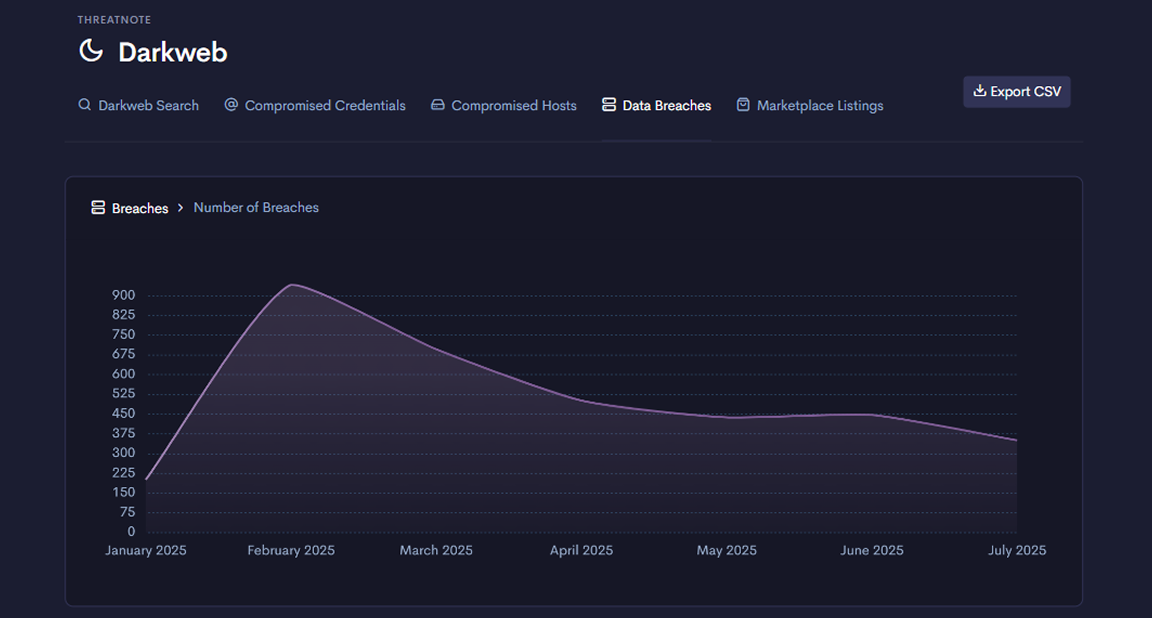



Threatnote transforms your CTI program by providing a single, unified platform for your entire team.
HERE'S HOW:



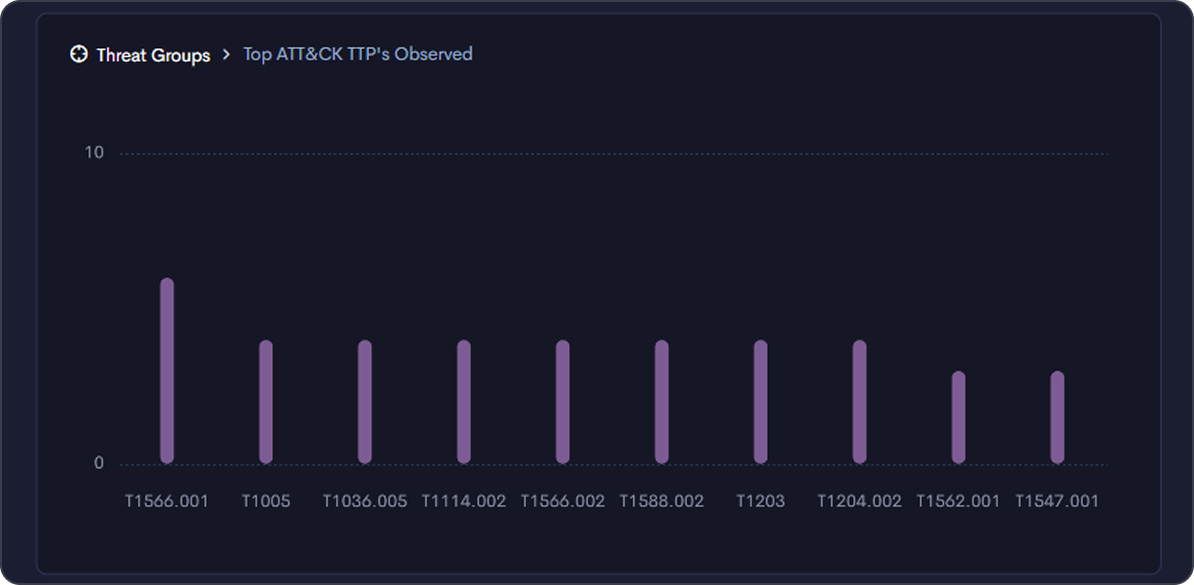
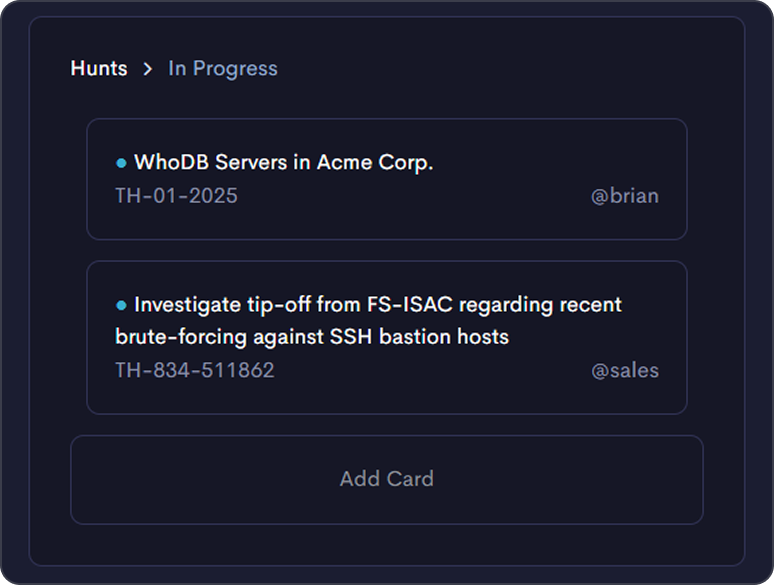
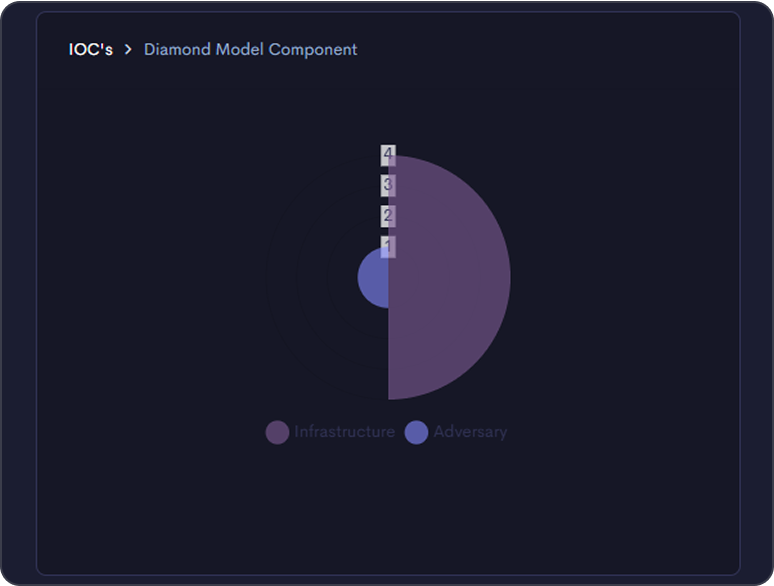
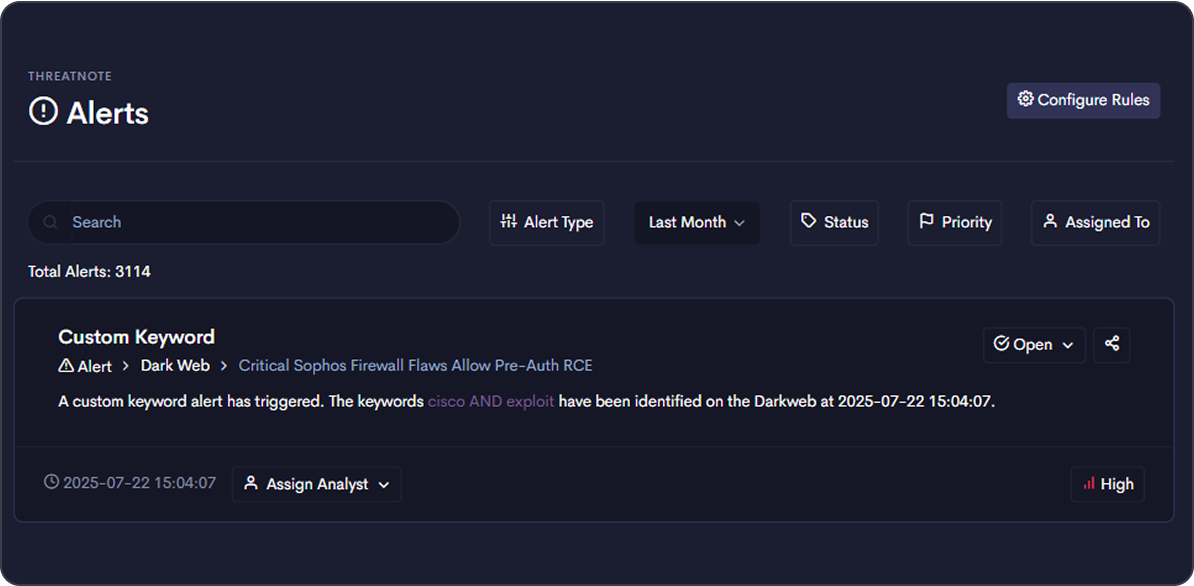
Move beyond noise
Threatnote brings clarity to your CTI program by centralizing workflows and surfacing metrics that show impact. From dark web trends to digital risk insights, your team gains visibility into what matters and the tools to act on it.

