
REQUEST A DEMO
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.

Morado discovered this campaign in September 2024 and published an initial blog detailing our findings in October. The purpose of this blog is to update our audience with additional information uncovered since that original publication.
Morado identified an active credential phishing campaign linked to the RaccoonO365 phishing-as-a-service (PhaaS) platform. The campaign, active since at least September 2024, distributes malicious PDF attachments impersonating HR and finance-related documents to harvest Microsoft 365 credentials and multi-factor authentication (MFA) codes. The attack chain utilizes PDF lures embedded with shortened lnk[.]ie URLs that redirected victims to highly convincing Microsoft login pages hosted on attacker-controlled typosquatted domains. All submitted credentials and authentication tokens are exfiltrated to actor infrastructure mimicking Microsoft’s API endpoints.
The campaign leverages RaccoonO365’s "Postman" mailer service to distribute phishing emails directly through compromised Microsoft 365 accounts using Microsoft Azure infrastructure, bypassing traditional email security controls. Analysis of the campaign’s targets suggests it is focusing on IT workers at organizations operating within global industrial supply chains, potentially providing the threat actors with access to large volumes of externally facing contacts that can be harvested using RaccoonO365’s integrated lead extraction tool. These leads may be used to support ongoing phishing operations or sold within the PhaaS ecosystem.
RaccoonO365 continues to evolve its operations, implementing new services such as the Postman mailer and lead extraction platform while shifting domain management and hosting responsibilities to affiliates. These changes improve operational resilience and reduce exposure while enabling affiliates to maintain stable phishing infrastructure that remains difficult to disrupt.
While investigating RaccoonO365, Morado discovered an active email phishing campaign attributed to one of their affiliates. Attribution was made after identifying a string unique to RaccoonO365 — “The gods are wise, but they do not know what you seeks” — present on the phishing domains. The campaign has been active since at least September 2024 and targets IT and service desk personnel at organizations operating within global industrial supply chains. In addition, the campaign uses a combination of compromised and spoofed email addresses to exploit the trust users place in well-known brands or services.
The operator has been using malicious PDFs designed to impersonate legitimate HR and finance-related documents, leveraging common workplace themes to exploit trust and urgency. The filenames mimic routine communications such as employee performance awards, invoices, benefits updates, and policy agreements. Some of these PDFs even use the name of the recipient such as “Performance_Award_Details_Mohammed.pdf,” making them appear more legitimate. This prompts the user to click on the attachment under the assumption that it is safe.

Once opened, the PDF attachment states that the file must be accessed online. This is accompanied by a reason for the inaccessibility, stating the file is encrypted or requires sign-in to view the resource. A button containing a shortened URL using the lnk[.]ie domain is displayed below the phishing message. The URL includes a five-character slug (e.g., /7AY07) that is used to resolve the malicious domain. By using a URL shortener, the threat actor obscures the true destination of the link. Users who hover over the button will only see the lnk[.]ie address, which increases the likelihood of click-through and successful redirection to the malicious site. However, clicking the button does cause a security warning to pop up on the user’s screen, which is an early indicator of phishing.


Once clicked, the lnk[.]ie link is opened in the user’s browser and subsequently resolved to the malicious URL. The user is presented with a Microsoft sign-in form hosted on a domain name similar to Microsoft services (e.g., microsoftclouddriveonline[.]com). These phishing pages do not host any static content; it is all loaded dynamically using an embedded <script> tag in the page’s HTML to avoid analysis and detection (discussed more later). In some cases, viewing the page source was prohibited indicating further anti-analysis techniques. The “Use Password” button is automatically selected for the form’s login method, allowing the threat actor to harvest all login information.
The user is first prompted to enter their email address. Strangely, after submitting it, they are asked to re-enter the same email on a slightly different-looking interface.


After entering their email twice, the user is prompted for their password.

Finally, if two-factor authentication (2FA) is enabled, the user receives a legitimate OTP code from Microsoft. After entering the code into the phishing page, all previously submitted information, including the email address, password, and OTP, is exfiltrated to an attacker-controlled endpoint designed to mimic Microsoft’s authentication infrastructure. The user is then either presented with an error message, redirected to office[.]com, or shown a blank page with no further action, effectively bringing the phishing chain to an end.
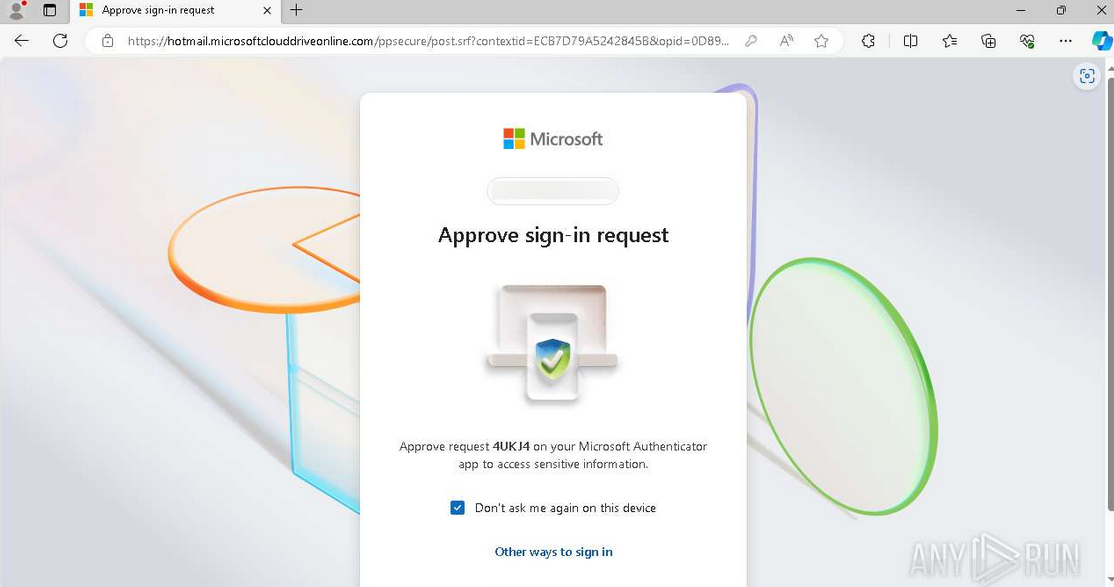
Analysis of the phishing flow indicates the use of adversary-in-the-middle (AiTM) reverse proxy techniques. After submitting credentials, victims with multi-factor authentication (MFA) enabled receive legitimate OTPs from Microsoft, confirming that valid credentials were forwarded to Microsoft's servers in real time.
In response to our last investigation and detection methods developed by LevelBlue, RaccoonO365 migrated its anti-bot logic from client-side scripts to server-side code to reduce exposure and prevent reverse engineering. The group also announced plans to integrate LevelBlue’s detection patterns into its backend filtering system, automatically blocking scans from their infrastructure. This marks a direct effort to evade security vendor monitoring and protect the stability of their phishing operations. However, as noted in the previous investigation, RaccoonO365 developers have consistently made errors that leave their services either vulnerable or non-functional. Our analysis was not hindered by the new system, though it is possible this specific campaign does not use it, as some of the malicious domains appear to predate its implementation.
The phishing page operates as a reverse proxy that closely emulates Microsoft’s login interface and authentication flow. It replicates elements such as PPFT tokens (Microsoft’s hidden anti-bot and session validation tokens), form field names (matching Microsoft’s real HTML input fields to avoid security tool detection), and staged UI transitions (the step-by-step login screens that mimic Microsoft’s multi-stage sign-in flow) while capturing credentials, authentication codes, and tokens in real-time. The attacker-controlled infrastructure forwards submitted data to Microsoft’s servers to complete authentication while simultaneously intercepting valid session data through replicated API endpoints, including /common/GetCredentialType, /oauth2/v2.0/authorize, and /ppsecure/post.srf.
As mentioned in the RaccoonO365 telegram channel, the PhaaS operation provides a “cloaking system” for its affiliates. In short, affiliates can disable the phishing content on their pages until after their phishing emails have been sent. This aids in bypassing email security as the embedded phishing links will not host any suspicious or malicious content at the time of scanning, allowing the message to pass through filters undetected. Once the email campaign is completed, phishing content is automatically restored to phishing pages.

This exact feature is controlled using a <script>tag embedded in the page:
(function () {
// Control variable to enable or disable the script
const enableScript = "on"; // Change to "off" to disable
let scriptActive = enableScript === "on"; // Track if the script should run
if (!scriptActive) {
return; // Exit if the script is disabled
}
RaccoonO365 phishing pages also support multiple languages. Victim browsers will detect their language and switch the page to match it using Office 365’s built-in auto-translate feature.


This campaign reused the same PDF files across multiple phishing emails. Specifically, PDFs named in the format “Performance_Award_Details_Recipient_Name.pdf” shared identical SHA-256 hashes, indicating an automated process in which the threat actor modifies certain fields, such as the filename, based on the recipient.
Although we successfully obtained all of the malicious PDFs identified, only two associated email files were recovered. The sending email address, notification@servicesystems[.]co, was used in both cases and belongs to a domain registered to a technology and consulting company based in South Africa. The recipients of the emails worked in different sectors (manufacturing and logistics), but both operated within global industrial supply chains and held positions related to IT or service desk functions. For emails that weren’t recovered, we identified additional victims through sandbox report screenshots, further indicating that the campaign is likely focused on targeting IT and service desk personnel.
It is highly likely that the notification@servicesystems[.]co account was previously compromised through RaccoonO365 phishing activity and subsequently leveraged for phishing distribution via their Postman mailer service. The following email addresses were also identified as senders in the campaign:
This campaign poses a significant threat to Office 365 users, particularly those in IT and service desk roles within industrial supply chains. By combining the use of compromised sender accounts with advanced adversary-in-the-middle reverse proxy techniques, the operators are able to harvest credentials, bypass multi-factor authentication, and capture valid session tokens for persistent access. The use of trusted email sources further reduces detection while increasing the likelihood of user interaction, making these phishing operations highly effective and difficult to mitigate.
RaccoonO365 has launched its Postman mailer service which we saw early signs of in our last investigation. This tool is designed to be used as a proprietary mailer that does not rely on SMPT and uses compromised Office 365 accounts to send mail using Microsoft Azure infrastructure. In short, rather than sending from an external email address, a legitimate, compromised email account is used, allowing threat actors to bypass security and spam filters.
Threat actors maintain persistent control of these compromised accounts using session cookies, or for greater persistence, refresh tokens. Cookies and tokens are obtained after the victim has been successfully phished. Refresh tokens allow the attacker to generate new access tokens without additional user interaction, ensuring stealthy persistence.

The Postman service includes several features designed to optimize email delivery and simplify operations for its users. It fully bypasses traditional SMTP protocols by sending emails directly through Microsoft Azure, using Microsoft's trusted IP reputation to achieve higher inbox placement and avoid spam filters. The tool supports plain text, HTML, and SVG attachments, while also offering automated email address extraction and auto-fill functionality to streamline bulk email campaigns. Postman requires only Office 365 cookies, which are converted into refresh tokens for authentication, removing the need for administrative privileges or credentials beyond the initial phishing stage.
A CLI-based Postman Client version is also available, offering an interface that enables easier automation and integration into larger spam operations. This client version is offered as part of a limited beta, bundled with a VPS setup to support stable, high-volume delivery.
RaccoonO365 affiliates who control more than 16 compromised Office 365 accounts are encouraged to operate as sellers, allowing other users to rent access to their accounts for email delivery through the Postman service.
RaccoonO365 is preparing to launch a new all-in-one lead extraction engine designed to automate the process of harvesting and sorting email leads directly from compromised Office 365 inbox sessions. The tool uses active session cookies to extract emails from 2FA and non-2FA accounts, with a built-in verifier that checks the validity and responsiveness of harvested emails. Extracted leads are automatically sorted and segmented by type, including Office 365 Business, Hotmail, Okta, GoDaddy, and ADFS. All harvested leads are centrally managed within a dashboard for efficient export and targeting. This allows affiliates to obtain additional leads from compromised accounts enhancing any future phishing campaigns.

RaccoonO365 maintains an active presence on Telegram where it shares operational updates with affiliates. Most notably, support for CloudFlare turnstiles was discontinued. This was one of the few early indicators of a RaccoonO365 phishing page. While expired domains still present a turnstile, it is likely future phishing domains will not.
Two announcements were also made regarding domain management and hosting infrastructure. First, domain management responsibilities have been delegated to affiliates rather than being managed directly by the RaccoonO365 operators. Secondly, RaccoonO365 operators will no longer provide free Virtual Private Servers (VPS) to affiliates due to high costs. Instead, the operators will offer VPS services for sale directly. As a result, while affiliates risk having their domains banned or revoked, their hosting infrastructure will continue to be resilient and difficult to take down.
Internally, the group operates a token-based payment system known as RaccoonO365 coins. These credits are managed through a Telegram-based coin transfer bot and are used to purchase access to tools and services within the RaccoonO365 panel. The system allows users to operate anonymously by avoiding traditional payment methods.

The active RaccoonO365 campaign poses a threat to IT workers at organizations operating within global supply chains. These accounts are likely targeted for their access and permissions within the environment, as well as their ability to generate a large number of potential leads due to their company’s role in global supply chains. RaccoonO365’s continuous development of new features, such as Postman and lead extraction services, provides its affiliates with streamlined, automated, and reliable phishing infrastructure. Their evasion techniques are also evolving, creating challenges for cybersecurity experts attempting to defend their organizations against phishing attacks and account compromises.
rule Malicious_RaccoonO365_Phishing
{
meta:
description = "Detects phishing PDFs containing lnk.ie links with 5-character slugs"
author = "jaydenpalacios"
date = "2025-06-16"
reference = "RaccoonO365 PDF phishing lures"
strings:
$lnk_ie = /lnk\\.ie\\/[A-Za-z0-9]{5}/
$pdf_header = "%PDF"
condition:
// Ensure it's a PDF file
$pdf_header at 0 and
// Look for the malicious lnk.ie pattern
$lnk_ie
}
title: RaccoonO365 Credential Phishing Activity (lnk.ie Redirection)
id: f2e90d91-4c49-4f5f-b73a-7c1d84cfa510
status: experimental
description: Detects users accessing phishing URLs consistent with RaccoonO365 lnk.ie redirection pattern.
author: jaydenpalacios
date: 2025-06-16
logsource:
category: web
product: proxy
detection:
keywords:
- 'lnk.ie/'
regex_patterns:
- 'lnk\\.ie\\/[A-Za-z0-9]{5}'
condition: keywords or regex_patterns
fields:
- url
- user
- src_ip
- user_agent
falsepositives:
- rare legitimate use of lnk.ie
level: high
tags:
- attack.t1566.002
- raccoono365
- phishing
- supply-chain



