
REQUEST A DEMO
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.

INC Ransomware is a mature ransomware-as-a-service (RaaS) operation that continues to expand in scope and activity. Affiliates rely on consistent intial access methods that exploit existing weaknesses rather than unique exploits. The operation remains effective because many organizations continue to expose vulnerable or misconfigured systems, use weak or stolen credentials, and fail to apply regular patching and hardening practices. Healthcare is the most affected sector due to its dependence on connected systems and the limited security resources available to many organizations. INC Ransomware is yet another example of how ransomware operations continue to succeed through common and preventable attack paths, including unpatched systems, exposed remote services, and weak authentication.
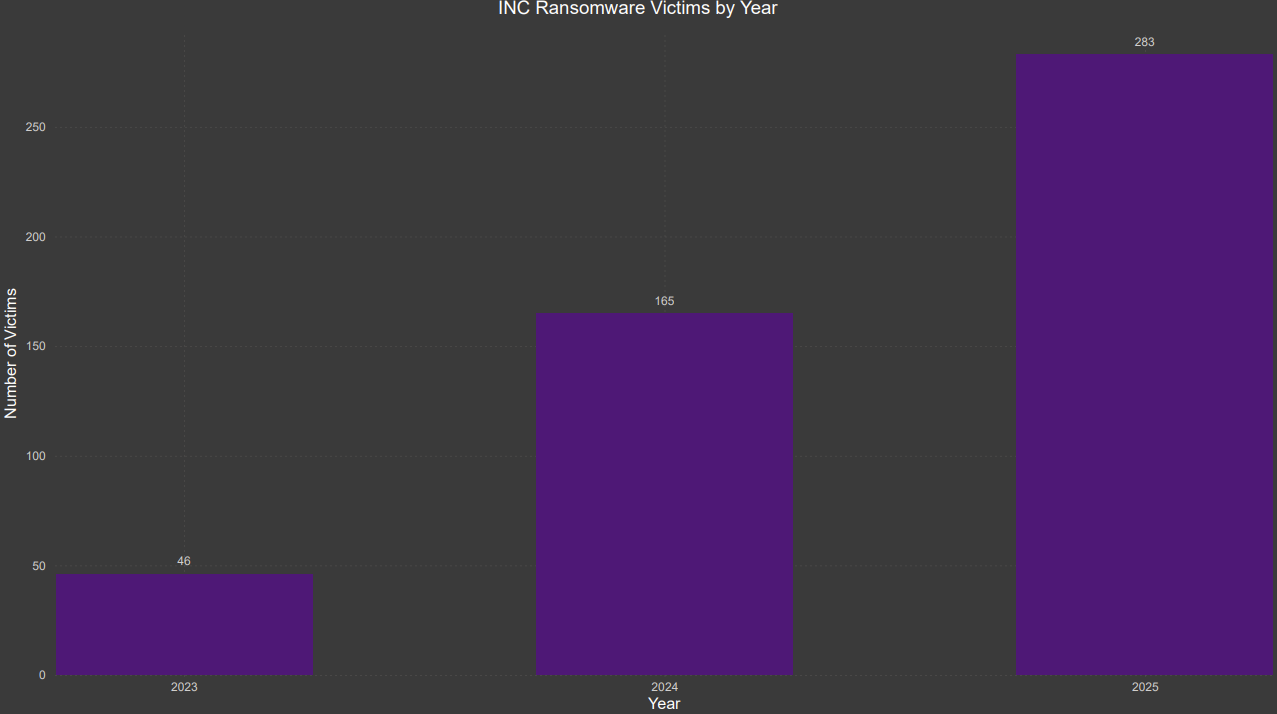
INC Ransomware is currently one of the most prolific RaaS operations in the threat landscape. It has consistently ranked among the top 10 ransomware groups since early 2025 and, in recent months, has become the third most active group, following Qilin and Akira. INC affiliates target a wide range of sectors across the globe. Healthcare is by far the most targeted sector and makes up over a quarter of their claimed attacks. Affiliates avoid organizations located in Russia, China, and other Commonwealth of Independent States (CIS) countries, reflecting the typical geographic targeting restrictions seen among ransomware operations based in Eastern Europe.
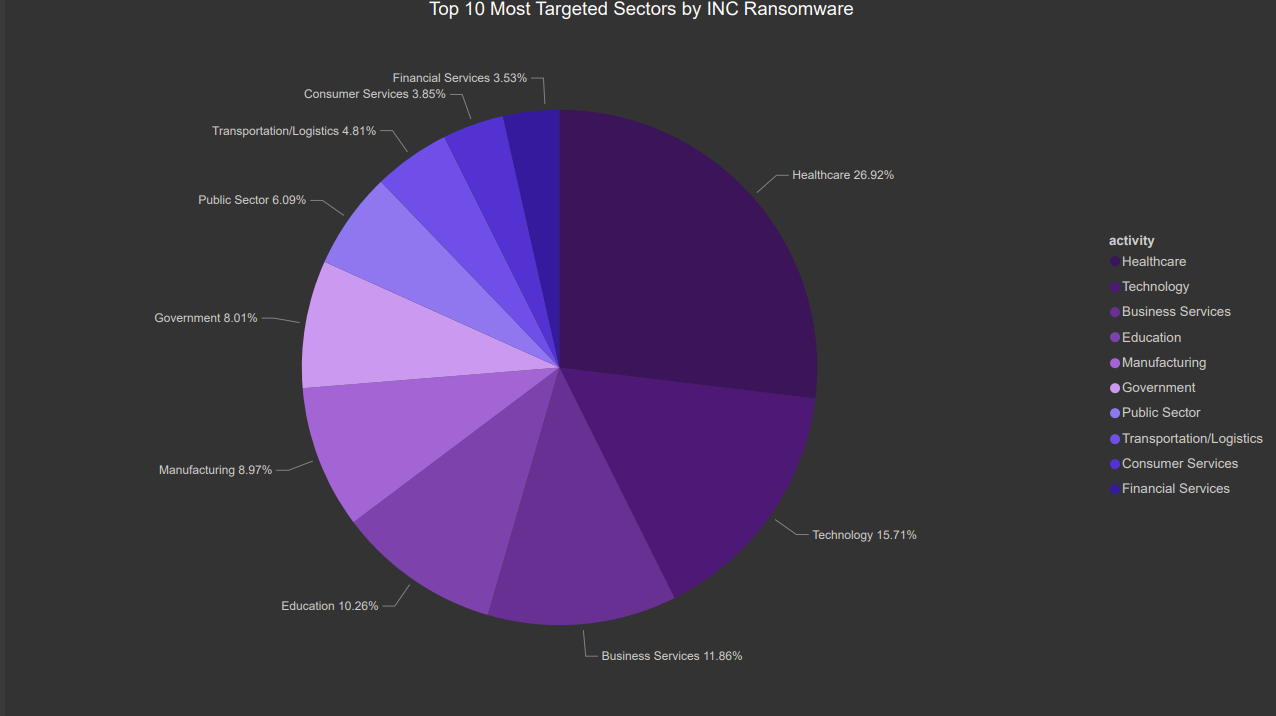
INC has seen a sharp increase in activity since its inception in 2023, more than doubling victim counts each year. In the past year, several large-scale incidents have amplified the group’s visibility, including the compromise of the Pennsylvania Attorney General’s Office in August 2025, where INC claimed to have exfiltrated over 5.7 terabytes of sensitive case data. Around the same period, INC also claimed responsibility for attacks against the Panamanian Ministry of Economy and Finance, alleging the theft of approximately 1.5 terabytes of fiscal and budgetary records. The group has also targeted healthcare entities, such as the Alder Hey Children’s Hospital in the United Kingdom, leaking patient and procurement data in late 2024.
Affiliates of the INC ransomware operation use common initial access techniques observed across multiple RaaS groups. Primary methods include credential theft through phishing campaigns, exploitation of unpatched vulnerabilities using publicly available proof-of-concept (PoC) exploits, and use of compromised credentials purchased from criminal marketplaces or Initial Access Brokers (IABs). INC affiliates also perform brute-force or credential-stuffing attacks against exposed RDP and SSH services.
The vulnerabilities exploited by INC affiliates primarily target Internet-facing perimeter network appliances. These devices include VPN gateways, firewalls, and application delivery controllers that manage remote access and control inbound and outbound network traffic. They are widely deployed across enterprise environments and are often easy to scan at scale using services such as Shodan or Censys. The following flaws have been exploited by INC affiliates:
Once compromised, these appliances provide attackers with a foothold inside the network. Since they process legitimate user sessions and encrypted traffic, malicious activity can blend in with normal network operations, reducing detection by intrusion detection systems (IDS) and security information and event management (SIEM) tools. Attackers can intercept credentials, capture session tokens, modify configurations, create new VPN accounts, and pivot laterally to internal systems.
Lateral movement is opportunistic and depends on each environment. However, there are limited details on methods used when targeting Linux systems, so for now, we will detail tactics used when targeting Windows. Affiliates harvest credentials and session tokens using techniques such as LSASS memory dumps, cached credential harvesting, and replication-style actions to obtain account hashes or Kerberos artifacts for pass-the-hash and pass-the-ticket attacks. They then use those credentials to access high-value hosts.
Attackers copy tools and archives between hosts using Windows file sharing (SMB) and admin shares (for example C$ and ADMIN$) and run them remotely. Affiliates deploy remote monitoring tools or backdoors that leverage legitimate management utilities. For example, operators have used PsExec, sometimes renamed to mimic system files, to run remote shells and install persistent backdoors. When edge devices are available, attackers pivot through modified VPN or routing settings, add routes, or create hidden tunnels to reach segmented networks.
The use of PsExec and similar utilities during the lateral movement stage also doubles as a persistence mechanism. While moving across the network operators install services, create scheduled tasks, register WMI subscriptions, or place renamed binaries in startup locations, ensuring persistent access to compromised machines.
INC affiliates remove forensic traces and disable defenses to hinder investigations. They use Windows utilities such as wevtutil to clear event logs and vssadmin to delete shadow copies, and operators have been observed using SystemSettingsAdminFlows.exe to disable Windows Defender. Attackers also stop or tamper with security services, rename or run legitimate admin tools under misleading names to evade detections, and install covert services or scheduled tasks to hide persistence.
Naturally, data exfiltration and encryption follow lateral movement and placement of ransomware binaries. Affiliates stage and archive data on compromised hosts with tools like 7-Zip or WinRAR and exfiltrate using legitimate sync and transfer tools such as rclone and Megasync to attacker-controlled cloud storage. Exfiltration supports double extortion because attackers both encrypt victim data and threaten to publish or sell stolen data on leak sites if the ransom is not paid.
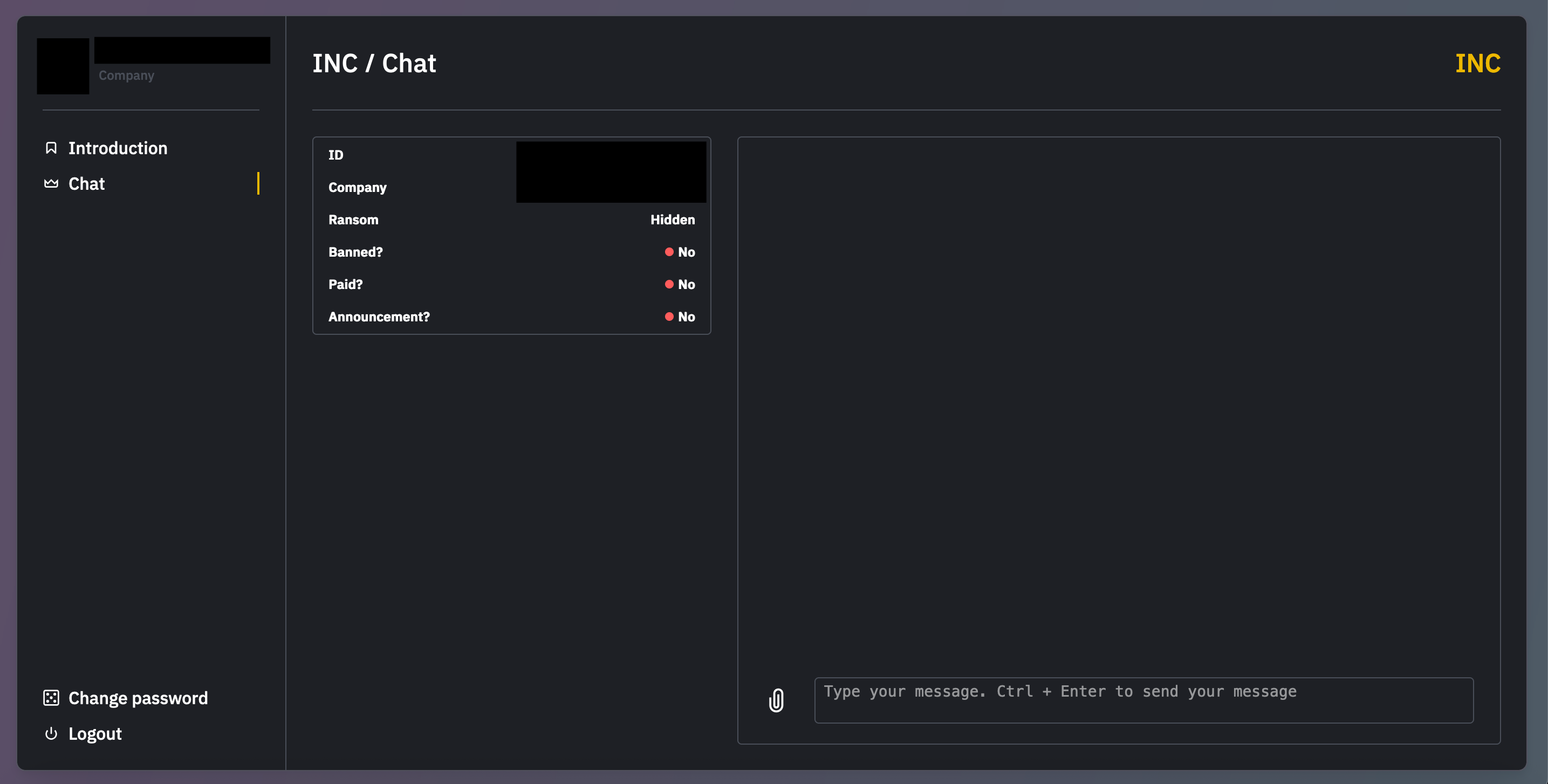
Ransom notes replace desktop wallpapers and are dropped on encrypted systems in both HTML and text formats (INC-README.HTML and INC-README.txt). Notes can also be printed physically using available printers. Each note includes a link to the ransom negotiation portal and a unique victim ID. Victims use this ID to register on the portal, where they are presented with an introduction to the INC operation. The tone is direct and unapologetic, framing the attackers as “penetration testers” motivated solely by money. The message references the group’s leak site to reinforce credibility and increase pressure during negotiations.
.png)
Victims are typically listed on the site only after negotiations fail or seven days after their first visit to the chat portal. Although in some cases, a countdown timer is displayed to threaten imminent publication of stolen data.
The ransomware locker malware itself has two known variants capable of targeting Linux and Windows systems. Locker executables have been observed named after the target OS. Examples include win.exe or windows.exe for Windows builds and lin.exe for Linux builds. Affiliates have also disguised lockers as JPEG files by changing the file extension to evade detection. Both variants are capable of multi-threaded encryption to encrypt machines at a faster rate to avoid detection. In one case, INC affiliates fully encrypted an enterprise environment within 48 hours of initial access, shrinking the window for an effective incident response.
The malware also attempts to delete shadow copies to prevent restoration of data.

A help menu is hardcoded into the locker binaries giving some insight into the flexibility of the execution options. These options allow for fine-grained control of the encryption process enabling the targeted encryption of files and network shares, hiding the console Window from users at their desktop, and even a choice of fast, medium, and slow encryption speeds.
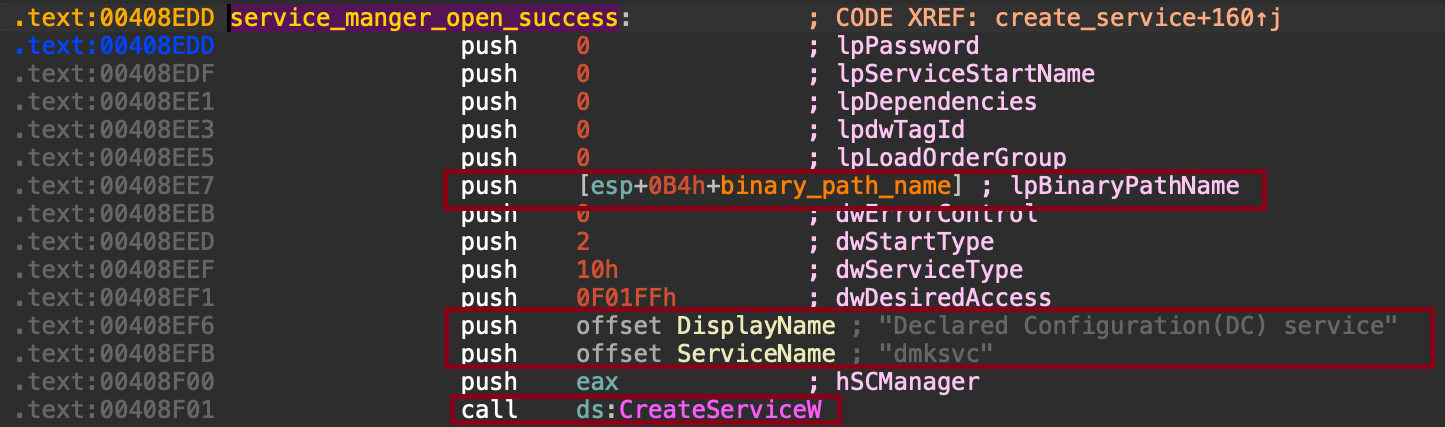
When ran in safe mode (–safe-mode), the locker also achieves persistence by creating a Windows service via the Service Control Manager. It calls CreateServiceW to register a service named dmksvc whose ImagePath (path for service to execute) points to the locker binary. The service is configured to run under LocalSystem and to start automatically, so the binary executes at boot.
The INC locker hardcodes its ransom note in the executable as a base64-encoded string. This artifact can be detected with YARA rules, but since affiliates commonly disable or tamper with security tools, organizations should focus on mitigating initial access methods instead.
The INC RaaS operation poses a significant threat to all sectors, but the risk is elevated for healthcare. The group disproportionately targets the sector, likely due to its reliance on digital systems for critical operations and the generally lower level of security among healthcare organizations resulting from limited resource allocation. In turn, this also affects third parties operating adjacent to the sector, who may experience indirect data exposure resulting from a healthcare breach.
Organizations looking to defend themselves from this threat should focus on limiting their attack surface and making an effort to mitigate potential initial access methods. This approach extends beyond this single RaaS operation and is applicable to defending against ransomware at large. Most initial access methods used by affiliates are opportunistic and overlapping, and include exploitation of unpatched or misconfigured systems, stolen credentials and credential reuse, phishing, purchasing access from initial access brokers (IABs), and brute-force attacks against services such as RDP, SSH, and VPN gateways.
rule Detect_INC_Ransomware_Strings
{
meta:
author = "Jayden Palacios"
description = "Detects the Base64-encoded header and key debug or print-related strings from INC ransomware samples, consistent since November 2024"
date = "2025-10-15"
strings:
// Base64 header from ransom note
$b64_fragment = "fn5+fiBJTkMgUmFuc29tIH5+fn4NCg0KLS0tLS0+IFlvdXIgZGF0YSBpcyBzdG9sZ" ascii
// Common runtime strings observed in INC locker builds
$s0 = "[+] Start encryption of directory: %s" fullword wide
$s1 = "[+] Sending note to printer: %s..." fullword wide
$s2 = "[+] Trying to open printer: %s..." fullword wide
$s3 = "[-] Failed to mount %s Error: %d" fullword wide
$s4 = "[+] Success! Closing printer: %s" fullword wide
$s5 = "[+] Start encryption of: %s" fullword wide
$s6 = "[%s] Encrypt network shares" fullword wide
$s7 = "[%s] Stop using process" fullword wide
$s8 = "[%s] Load hidden drives" fullword wide
$s9 = "[+] Found drive: %s" fullword wide
$s10 = "[+] Encrypting: %s" fullword wide
$s11 = "[+] Mounted %s" fullword wide
$s12 = "[%s] Debug" fullword wide
$s13 = "[*] Loading hidden drives..." fullword wide
$s14 = "Microsoft Print to PDF" fullword wide
condition:
$b64_fragment or any of ($s*)
}
Since each locker executable has a specific ID for their victim, file hashes aren't an effective means of detecting INC Ransomware as they are not reusable. However samples can be used to build better detections such as the YARA provided rule above.