
REQUEST A DEMO
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
Amadey is a modular Windows malware sold as Malware-as-a-Service since 2018 that functions as both a botnet client and a flexible loader, allowing low-skill operators to deploy stealers, cryptominers, and RATs via phishing, malvertising, and trojanized installers. It is commonly delivered though social engineering methods such as phishing and malvertising. The malware makes attempts to hinder analysis but tools have been developed by researchers that allow nullify the obfuscation. Amadey offers plugins to expand capabilities, allowing threat actors to proxy network traffic, monitor the infected user’s clipboard, and even steal credentials and artifacts from browsers, crypto wallets, and many other applications. The analyzed sample revealed the use of AS209800 as infrastructure for its malicious operations as well as a wide host of other malware families. As a widely used as a loader for secondary payloads, Amadey poses a significant operational risk and can be leveraged to deliver more damaging payloads such as ransomware.
Amadey is a modular Windows-targeting malware that operates as both a botnet client and a loader for secondary payloads. Since 2018, its author, known by the alias "InCrease," has been advertising and selling Amadey as Malware-as-a-Service (MaaS) on dark-web forums such as XSS and Exploit. A lifetime license for the malware costs $600, with an additional $50 fee for each rebuild and $50 for every new C2 installation. The C2 installation fee indicates infrastructure needed to launch attacks using Amadey are provided by its operator(s).
As a MaaS offering, it is distributed in a variety of methods. Any threat actor who can afford a license is able to launch an attack regardless of technical expertise. Due to this fact, it is most often delivered using social engineering methods such as phishing, malvertising, ClickFix attacks, and trojanized software.
As a loader, Amadey is one of the most frequently used in multi-stage infection chains involving various malware families. It is sometimes deployed by other loaders such as SmokeLoader, which may seem redundant, but is due to Amadey’s more advanced capabilities. However, it mostly functions as a first stage loader. Amadey most often delivers Lumma and StealC but has also been observed deploying multiple families of infostealers, cryptominers, and remote access trojans (RATs).
Amadey uses a C++ agent with a PHP/SQL control panel to deliver and manage payloads. The agent supports per-host tasking (send commands to an individual machine), controlled download and execution of secondary payloads with up to three retries, custom DLL execution via rundll32, MSI silent install, and reboot-persistence. It fingerprints infected machines and exfiltrates the data to the panel that separates progress, errors, and confirmed launches.
The malware implements a plugin-based architecture managed from its PHP/SQL C2 panel. Operators can push, enable, disable, or remove plugins on a per-host basis and assign plugin-specific tasking via the panel. Plugins are delivered as separate payloads and loaded into isolated subprocesses or invoked through rundll32 for DLL execution.
Plugin types observed include a reverse proxy to obfuscate network traffic, a clipper that monitors clipboard activity to intercept cryptocurrency transfers, and a stealer that collects browser and application artifacts from a long list of targets (Chrome-based and Firefox browsers, Tor, Pidgin, Gajim, Psi+, WinSCP, FileZilla, Outlook, Thunderbird, multiple desktop wallets, and Telegram sessions). Plugin configuration and telemetry are trackable per host which supports targeted tasking.
Amadey obfuscates strings used in the malware to hinder static analysis. However, this is mostly a simple deterrent as decrypting the strings is fairly simple. To obfuscate its strings, Amadey encodes them using base64 and then uses a polyalphabetic cipher to encrypt the encoded strings. The author first encodes plain strings with base64 and then encrypts the resulting text with a simple polyalphabetic cipher. A single hardcoded key is required because the loader must be able to decrypt strings at runtime. This string-encryption method and key-recovery process were previously documented by malware researcher 0x0d4y, enabling easier analysis for other researchers.
Finding the key is trivial. It appears in the binary alongside two other values (RC4 key for C2 traffic encryption and a campaign ID) and all three follow the same storage pattern, so a strings dump or a quick static scan typically exposes them. To recover a string, apply the polyalphabetic decryption using the discovered key, then base64-decode the result to obtain the original cleartext. 0x0d4y also published an open-source Amadey string decryption tool that automates this process and assists in the analysis of obfuscated content.
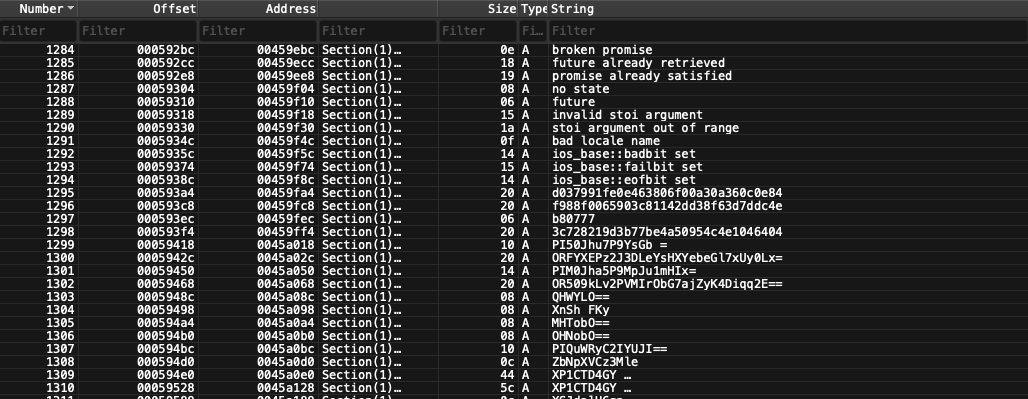
Using the decryption tool reveals the obfuscated strings contain IP addresses and endpoints for command and control servers that are managed using the previously mentioned panel. Also revealed in this specific sample is the clipper plugin used for monitoring the machines clipboard.
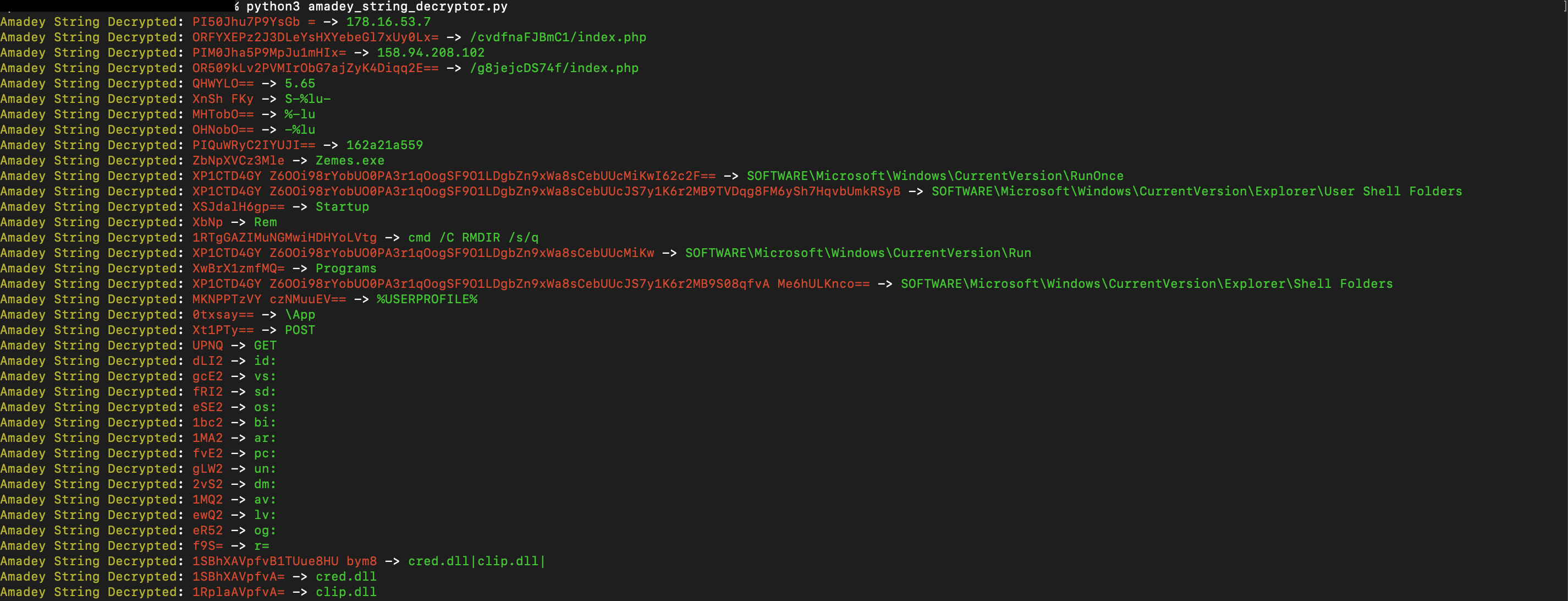
The decrypted strings above were extracted from an Amadey sample collected in the wild. Analysis shows this sample is a first-stage dropper that embeds two additional binaries. The first executable, swibu.exe, was identified as a member of the Kepavll trojan family. The second executable, syshost.exe, is a second-stage Amadey component that contains stealer and clipper modules, as indicated by strings referencing cred.dll and clip.dll in the file contents. The first stage of Amadey also adds the following Windows registry entries pointing to the two dropped files to achieve persistence and ensure they are ran even after reboot:
swibu.exesyshost.exeThe file named swibu.exe, associated with trojan malware, was persisted using the following command to created a scheduled task named “Google Chrome DeskUpdate” that runs every minute:
```powershell
"C:\Windows\System32\schtasks.exe" /create /sc minute /tn "Google Chrome DeskUpdate" /tr "C:\Users\admin\AppData\Roaming\swibu.exe”
```The second stage of Amadey (syshost.exe) registers a COM class (CLSID) in the Windows registry and ensures the malicious binary is used as the COM server. When legitimate code calls CoCreateInstance or other COM activation APIs for that CLSID or ProgID, Windows loads the attacker-controlled server. This gives the malware automatic execution in normal OS workflows that instantiate COM objects, and it persists across reboots because the registration is stored in the registry.
The malware collects basic information about the infected machine including the PC name, operating system used, anti-virus installed, and other information that could be useful to threat actors. It exfiltrates the data to two command-and-control servers whose addresses are stored in the binary’s encrypted strings. The redundancy ensures that even if one C2 server was disrupted, the malware can still function properly using a fallback. The endpoint used is typically a series of random characters followed by the /index.php slug. The data is encrypted with the RC4 key recovered from the sample’s Strings output. Because RC4 is symmetric, the same key can be used to decrypt the captured traffic and reveal the exfiltrated information. The tool used to decrypt Amadey traffic can be found here.
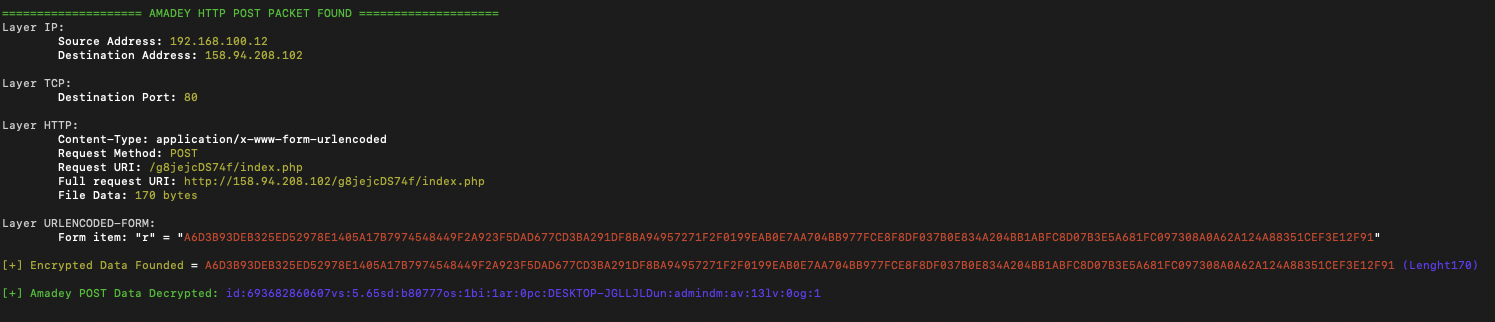
The IP addresses in the Amadey traffic align with those seen in the decrypted strings output:
178.16.53[.]7 is also used as a C2 address for the AsyncRat malware. It may also be used as TinyLoader infrastructure, but its possible this sample below was a part of an Amadey infection chain.
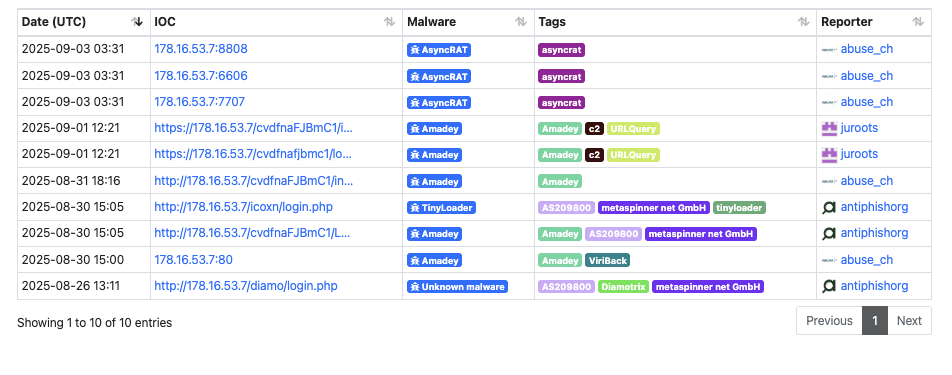
Both IP addresses belong to AS209800 (metaspinner net GmbH). The network has been associated with command-and-control (C2) infrastructure for multiple malware families, including Orcus RAT, AsyncRAT, Remcos, Hook/HookBot, XWorm, Latrodectus, Rhadamanthys, and SectopRAT, as well as the open-source and commercial C2 frameworks AdaptixC2 and Cobalt Strike. Further analysis of AS209800 revealed numerous phishing domains hosted within the same ASN, indicating that it functions as a high-risk provider used for both C2 operations and credential-harvesting infrastructure.
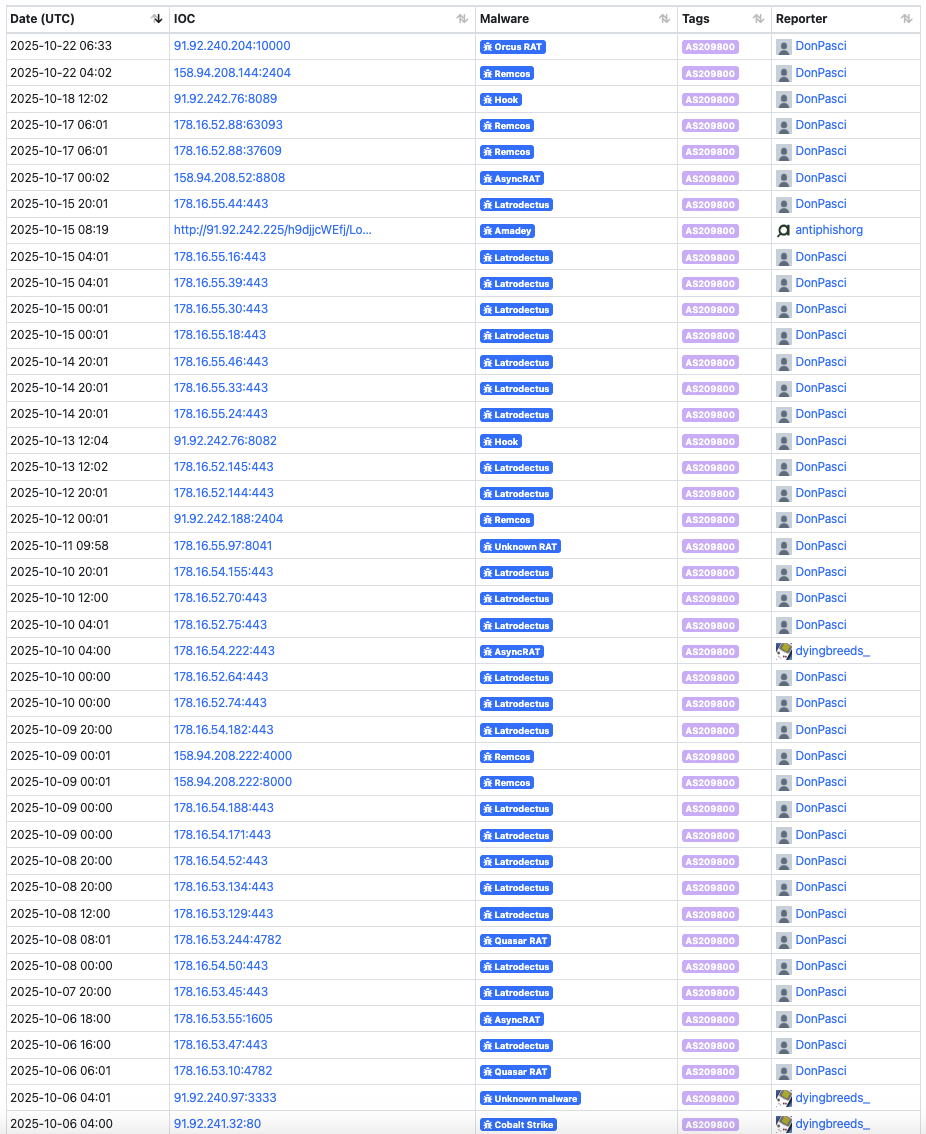
Organizations should consider blocking traffic to AS209800. This can effectively disrupt malware operations that rely on fallback command-and-control (C2) servers within the same ASN rather than distributing their infrastructure across multiple networks.
Amadey continues to serve as a persistent threat in the cybercrime ecosystem due to its accessibility, modular design, and ability to act as both a botnet client and a loader for secondary payloads. Its active use across numerous campaigns underscores its reliability and continued development. The malware’s plugin system enables operators to selectively deploy capabilities such as credential theft, clipboard hijacking, and reverse proxying, increasing its flexibility across various attack scenarios. The analyzed sample demonstrates how Amadey serves as an initial infection stage for broader payload deployment, including information stealers and remote access trojans. The shared infrastructure within AS209800 and overlap with other malware families indicates a centralized ecosystem of threat actors leveraging common service providers for C2 operations. As a result, Amadey remains a critical enabler in multi-stage intrusion chains that can lead to ransomware deployment or large-scale data theft.