A team of researchers from Georgia Tech, the University of Michigan, and Ruhr University Bochum has created a novel attack termed "Hot Pixels," which can retrieve pixels from the content displayed in the target's browser and infer the navigation history.
Even with the most recent side-channel countermeasures enabled, the attack uses data-dependent computation durations on modern system-on-chips (SoCs) and graphics processing units (GPUs) to covertly extract information from visited web pages on Chrome and Safari.
The researchers observed that contemporary processors have difficulty reconciling high execution speeds with their power consumption and heat dissipation constraints. This results in distinct patterns of behavior that indicate specific instructions and operations.
These patterns are easily detectable via internal sensor measurements that are frequently accessible via software and, depending on the type of device, can aid in identifying what is viewed on the target device with an accuracy of up to 94%.
Mapping the CPU performance of modern devices
By analyzing frequency, power, and temperature measurements on modern devices, the researchers came to the conclusion that passively cooled processors may reveal data via power and frequency measurements, whereas actively cooled chips leak data via temperature and power measurements.
The researchers evaluated Apple M1 processors, Cortex-X1 Arm CPUs on a Google Pixel 6 Pro, and Qualcomm Snapdragon 8 Gen 1 on a OnePlus 10 Pro. They mapped the thermal limits (throttling sites) and correlated responsibilities with distinct frequency and energy consumption metrics.
The researchers then examined data-dependent leakage channels on discrete and integrated GPUs, such as Apple's M1 and M2, AMD Radeon RX 6600, Nvidia GeForce RTX 3060, and Intel Iris Xe.
This information was used to evaluate the "Hot Pixels" attack.
Chrome 108 and Safari 16.2, the most recent versions available at the time of the study, with their default configurations and side-channel countermeasures enabled, were used to evaluate the "Hot Pixels" attack.
The configuration restricts the power and temperature of the CPUs so that information regarding the color of the pixels displayed on the target's screen (white or black) is transmitted via the frequency of the processor.
The attack mechanism involves utilizing SVG filters to induce data-dependent execution on the target CPU or GPU, followed by measuring the computation time and frequency with JavaScript to infer the pixel color.
Researchers collect pixels from an unaffiliated target website using an i-frame element on a page controlled by an assailant. The contents of the i-frame, which likely contain confidential information about the victim, are concealed but can be calculated by applying an SVG filter and measuring rendering times.
The accuracy of the observations varied between 60% and 94%, and the time required to decode each pixel ranged between 8.1 and 22.4 seconds. The AMD Radeon RX 6600 was the "leakiest" device, while Apple's devices appeared to be the most secure.
Safari is not vulnerable to the attack described in the preceding section because it prevents cookie transmission on i-frame elements from origins other than the parent page. Therefore, the pixels embedded within the i-frame will not contain any user-specific information. However, the researchers discovered that Safari is vulnerable to a subtype of the Hot Pixels attack that can compromise the user's privacy by identifying their browsing history.
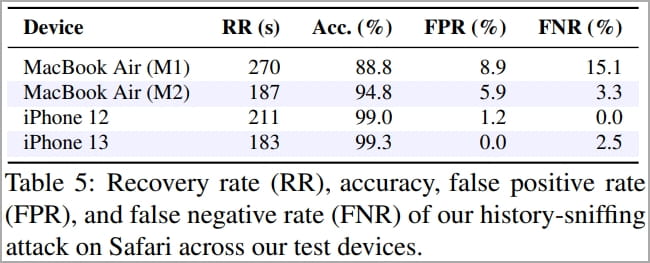
The devised method entails posting links to confidential pages on a website under the attacker's control and then using the SVG filtering technique to infer the color, therefore, the fundamental Hot Pixels principles can be used to infer the target's browsing history. In addition, because the entire hyperlink would have the same color, recovering a single pixel from each would suffice, enabling rapid parsing of extremely extensive lists of hyperlinks. On iPhone 13, this attack captured data with a 99.3% accuracy rate, a 2.5% false-negative rate, and a recuperation time of 183 seconds per 50 hyperlinks.
Conclusion
In March, the researchers shared their findings with Apple, Nvidia, AMD, Qualcomm, Intel, and Google. Every vendor has acknowledged the issues and is actively working to rectify them.
Hot Pixels attacks are only effective on devices that obtain a stable power consumption state rapidly, such as smartphones, despite the fact that the data leak throughput is typically low.
However, affected vendors and stakeholders are already contemplating potential solutions to the identified problems, such as limiting the use of SVG filters on i-frames in the HTML standard.
Currently, the Chrome team is implementing Safari's cookie isolation mechanism, which inhibits the loading of cookies on orphan i-frames.
There are also proposals to restrict OS-level access to sensors that provide thermal, power, and frequency readings to unauthorized users.